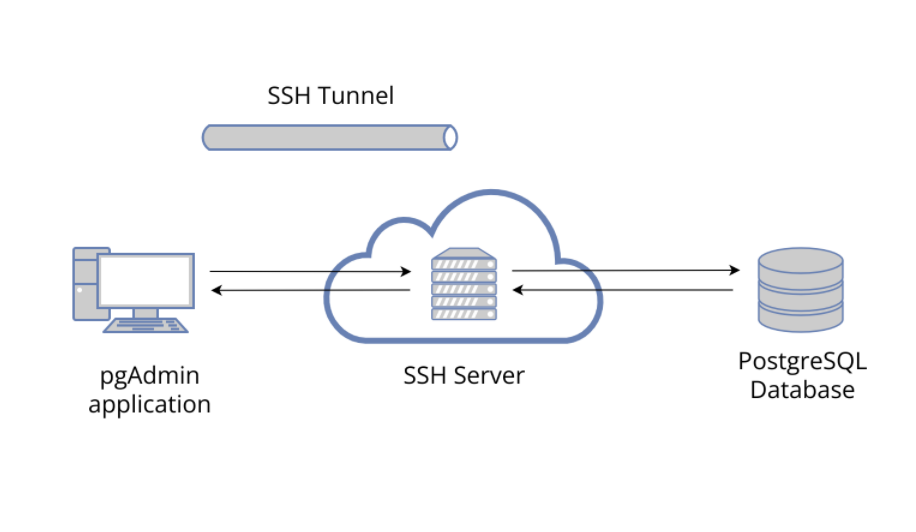
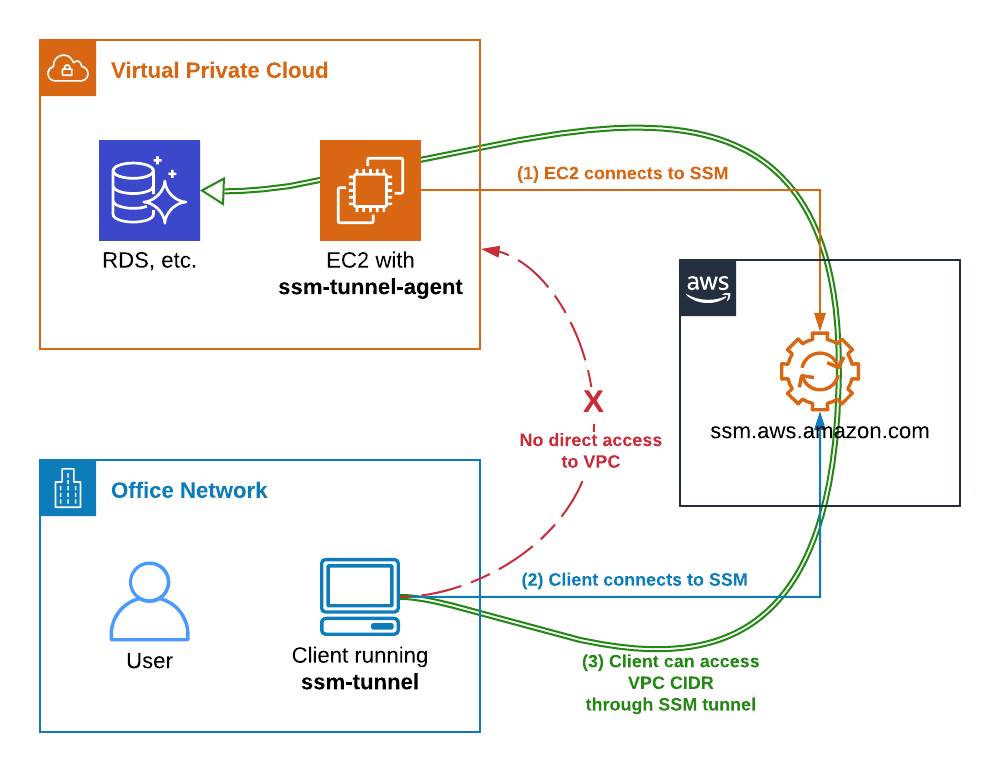
Step by Step Introducing to AWS IoT Secure Tunneling and Pricing Details(00)

This image is part of a curated gallery related to How To Securely Access Aws Iot Devices Using Ssh Tunneling Techniques. All visuals are selected to provide relevant visual reference for the topic.
Image gallery: How To Securely Access Aws Iot Devices Using Ssh Tunneling Techniques